Help Admin Adding a monitor Server Resource Check Profile
Resource Check Profiles can be used to monitor a resource on the server using server monitors. The resources to be monitored are added as checks to a resource check profile and this profile can be associated with any number of server monitors. To associate this profile to a server monitor, go to edit monitor page.
The URL resource check lets the user monitor the availability of a local URL on a server. To configure this, a check name must be given and the URL to be monitored must be entered. The URL value must begin with either http:// or https://. This can be followed by the host name and optionally, the port [https://host:8080]. The host name can be given as localhost or the machine name can be specified. If unsure about the machine name or if the same profile is to be applied to multipe server monitors, then the host name can be denoted as $$HOSTNAME$$. This will be replaced with the respective server host name as needed.
Alternatively, 127.0.0.1, the local IP address of the machine can be given in place of the hostname. Alternatively, the IP address can be configured in the check as $$IP$$. This will be replaced by the IP address of the respective servers. To avoid redundancy duplicate URLs cannot be added in the same resource profile. [https://$$IP$$:8444]
Examples for URL include:
http://I27.0.0.1:8080
http://localhost
http://$$HOSTNAME$$:8080
http://$$IP$$
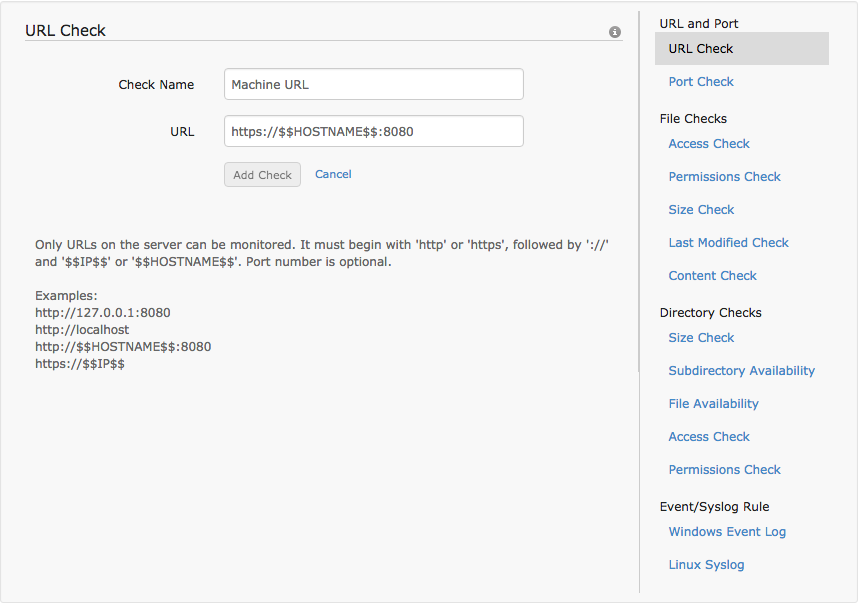
Port number is optional.
When the configured URL is down, the check is marked as down and the monitor status is changed to trouble if you configured the threshold in threshold profile.
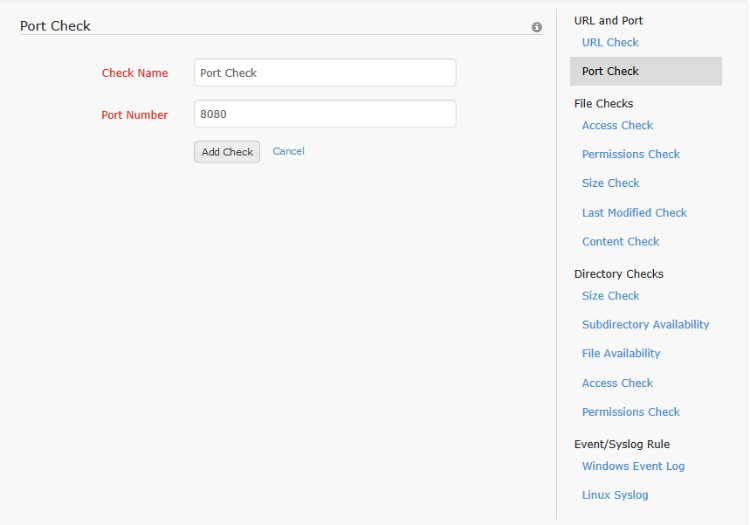
This resource check allows the user to monitor ports in a server. The ports to be monitored can range from 0 to 65535. Duplicate ports cannot be added in the same resource profile to avoid redundancy. To add this check to a resource profile, the check name and the port number must be configured add 'Add Check' has to be clicked and the profile has to be saved.
When the configured port goes down, the monitor status is changed to trouble if it was previously up.
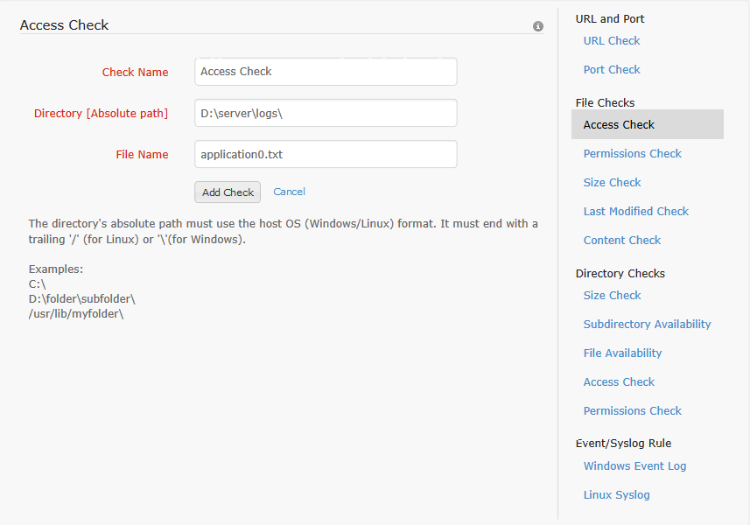
The file access check allows the user to watch some file and be alerted whenever the file is accessed. To configure this check, click on Access Check under File Checks in the right hand menu. Configure the check by assigning a check name, the absolute path to the file on the server and the file name. In this check, the file name supports regular expressions [For information on regular expressions click here]. Using regular expressions, the user can watch for multiple files with names matching a pattern.
If access check is applied to a file/directory which is already being watched in polled checks [content check, size check], then it will keep on notifying every 5 mins as those files/directories are accessed to perform polled checks data collection.
When notified, the monitor status will be changed from up to trouble. If the monitor is already in trouble or down state, no status change occurs. For access check, the trouble status will last for one poll duration after which the status will be reset.
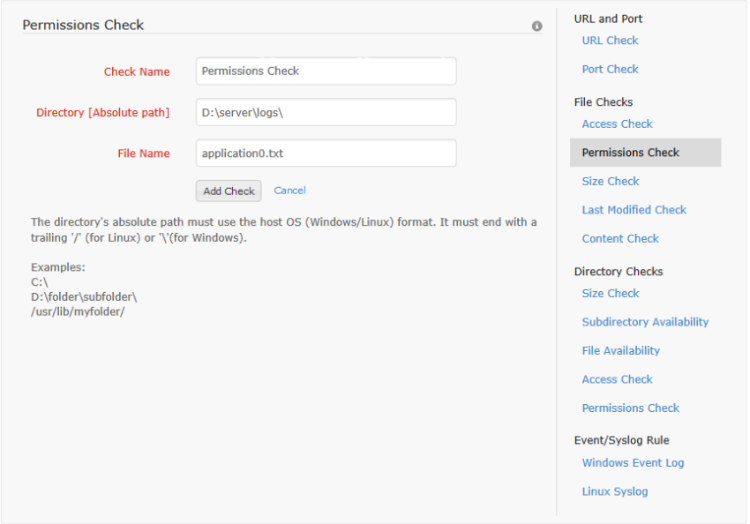
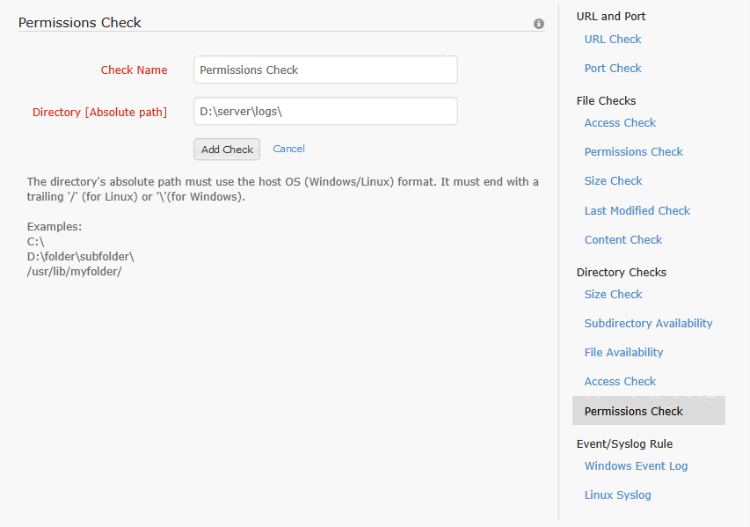
The user can monitor whether the permission of a file has been modified by configuring this check. To configure the permissions check for a profile, the check name, path to the file and the file name have to be given. The file name supports regular expressions [For information on regular expressions click here]. Once this check is associated with a server monitor, the user will be alerted if the specified file's permission attributes change. This alert causes the monitor to switch from Up to Trouble status, if it isn't already in trouble or down state. For permissions check, the trouble status will be maintained for one poll duration. After that the monitor status is changed back to up.
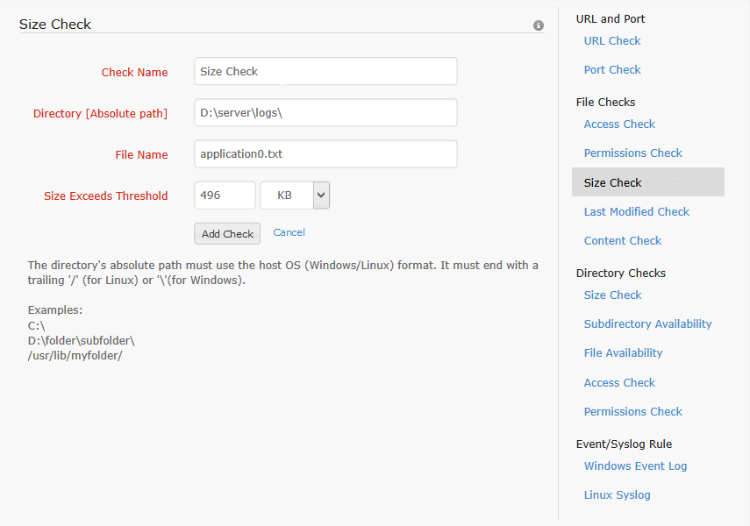
The size check enables the user to monitor the size of the file and be notified when it exceeds a threshold. The size check is configured using the path to the file, the file name and the file size threshold. The file name supports regular expressions [For information on regular expressions click here]. The file size can be specified as a whole number and a size unit is selected. The size unit conversion used is as follows -
1KB =1000 Bytes
1MB=1000 KB
1GB=1000MB
Once this check is configured, the specified file(s) size is checked periodically and an alert is sent when the size exceeds the configured threshold. This alert causes the monitor to switch from Up to Trouble status, if it isn't already in trouble or down state.
For the monitor status to be affected, 'Generate trouble alert when a resource check fails' must be set to 'Yes' in the server's associated threshold profile. To know more about configuring threshold profile, click here.
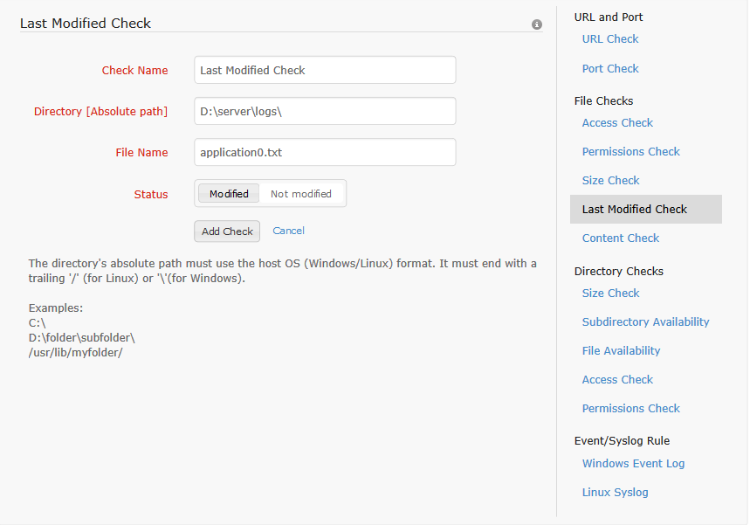
The last modified check can be configured for files. This alerts the user in either of two cases - if the file is modified by a user / if the file is not modified for more than a set period of time. To configure this check, the check name, path to the file, the file name (or regular expressions, and the status of the file for which the alert is to be triggered must be configured. If the status is configured as 'Not Modified', additionally the maximum time duration for which the file can stay unmodified is to be configured. The alert causes the monitor to switch from Up to Trouble status, if it isn't already in trouble or down state. The trouble status is maintained for one poll duration after which the status of the monitor is reset to up.
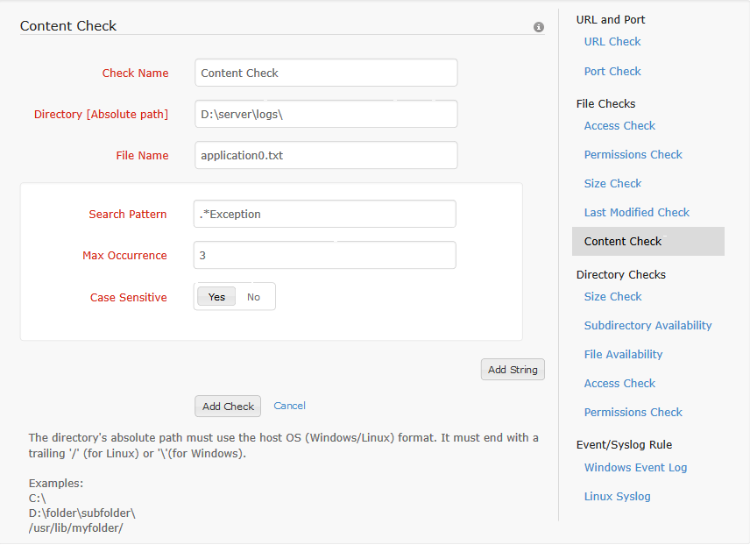
Content check is used to search a file for some text/content. The absolute path to the directory containing the file and the file name are given. Also, one or more search strings are configured for the check. For each search string, the search pattern, maximum occurrence and case sensitivity parameter are configured. The check is added only if at least one search string is configured for the content check. In content check both file name and search pattern support regular expressions.
If the search string occurs over a set number of times (max. occurrence), the alert is triggered. This alert changes the monitor status to trouble from up if the monitor isn't already in trouble or down status. The trouble status is maintained for one poll duration after which the status of the monitor is reset to up.
In content search check, the last scanned position is noted. The subsequent scan starts from the previously scanned position.
The directory size check is used to notify when a directory on the server file system exceeds a size threshold. To configure this check, the check name, the path to the directory to be monitored and the size threshold with unit must be given. The size unit conversion used is as follows -
1KB =1000 Bytes
1MB=1000 KB
1GB=1000MB
When the size of the directory exceeds the given threshold, an alert is raised. This alert changes the monitor status to trouble from up if the monitor isn't already in trouble or down status.
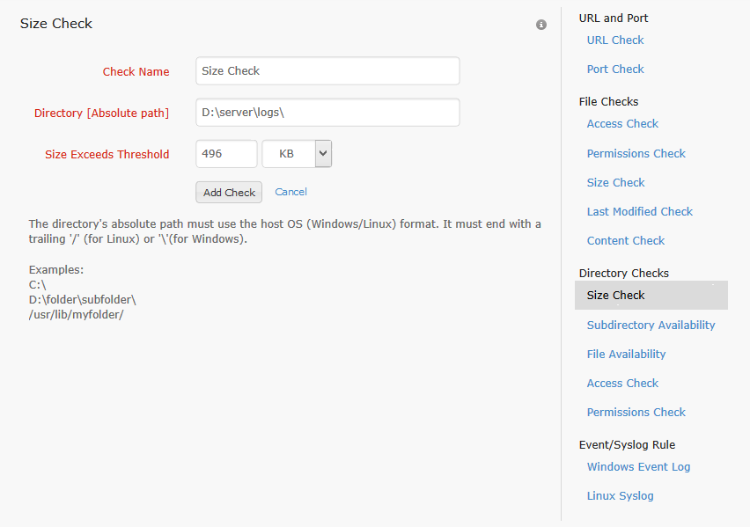
For the monitor status to be affected, 'Generate trouble alert when a resource check fails' must be set to 'Yes' in the server's associated threshold profile. To know more about configuring threshold profile, click here.
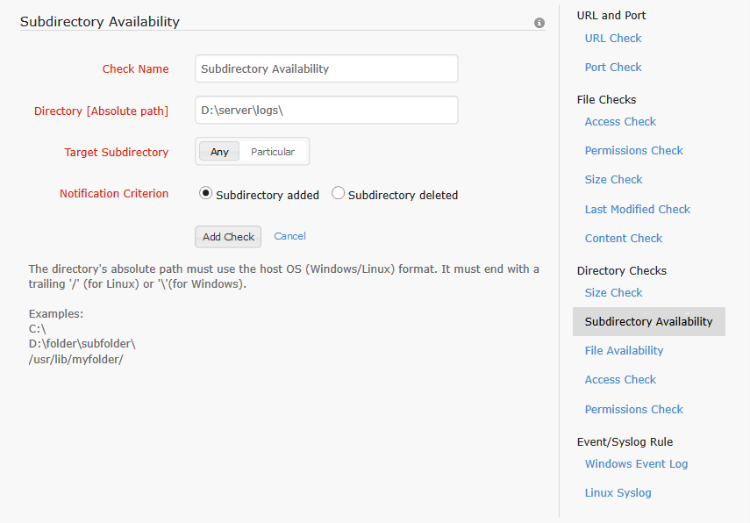
The sub directory check is used to monitor all the sub directories within a monitored directory. The user has the option to monitor all the sub directories or a particular sub directory [subdirectory name supports regular expressions] under the specified directory. The user can watch for the addition or deletion of the sub directory. The alert is raised when the configured event occurs and the monitor status is set to trouble if it isn't already in trouble or down state].
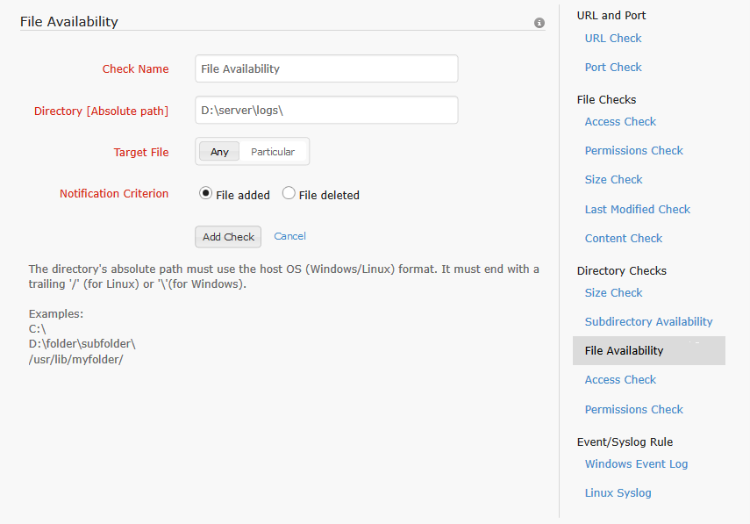
The file check is similar to the subdirectory check. The file check is applied to files instead of folders within a directory. Here too, the user has the option to watch for either all the files or a particular file [file name supports regular expressions] within the specified directory. Addition or deletion event can be monitored. When the file(s) is added/deleted, as per the configured check, the alert is sent and the monitor status is set to trouble if the monitor isn't already down or in trouble state.
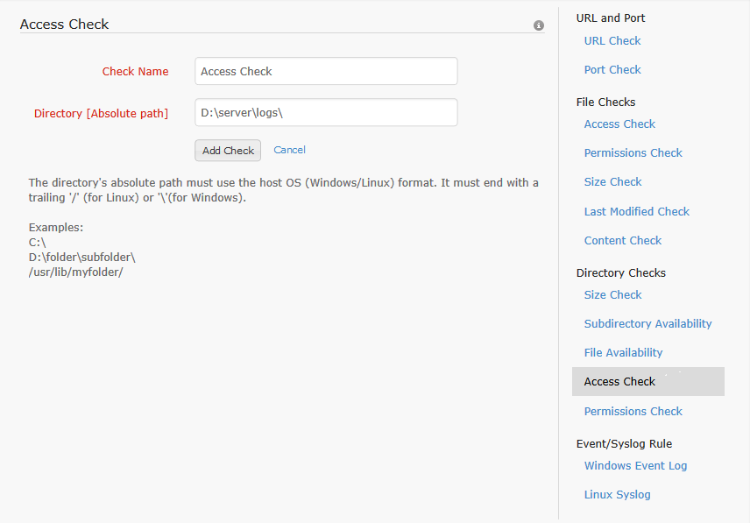
This allows the user to monitor a directory and be notified when it is accessed for any reason. The absolute path to the directory to be monitored is configured in the directory access check. When this check is applied to the server monitor, the directory is watched for access. When accessed, the alert is raised and the monitor goes to trouble status from up. The status is unaffected if the monitor status was previously trouble or down. The trouble status is maintained for one poll duration after which the status of the monitor is reset to up. If access check is applied to a file/directory which is already being watched in polled checks [content check, size check], then it will keep on notifying every 5 mins as those files/directories are accessed to perform polled checks data collection.
The permissions check can be configured for the directory. If the permission attributes of the watched directory is modified, this will be notified by the agent. The event will be logged and the monitor status will be set to trouble if it was previously up. The trouble status is maintained for one poll duration after which the status of the monitor is reset to up.
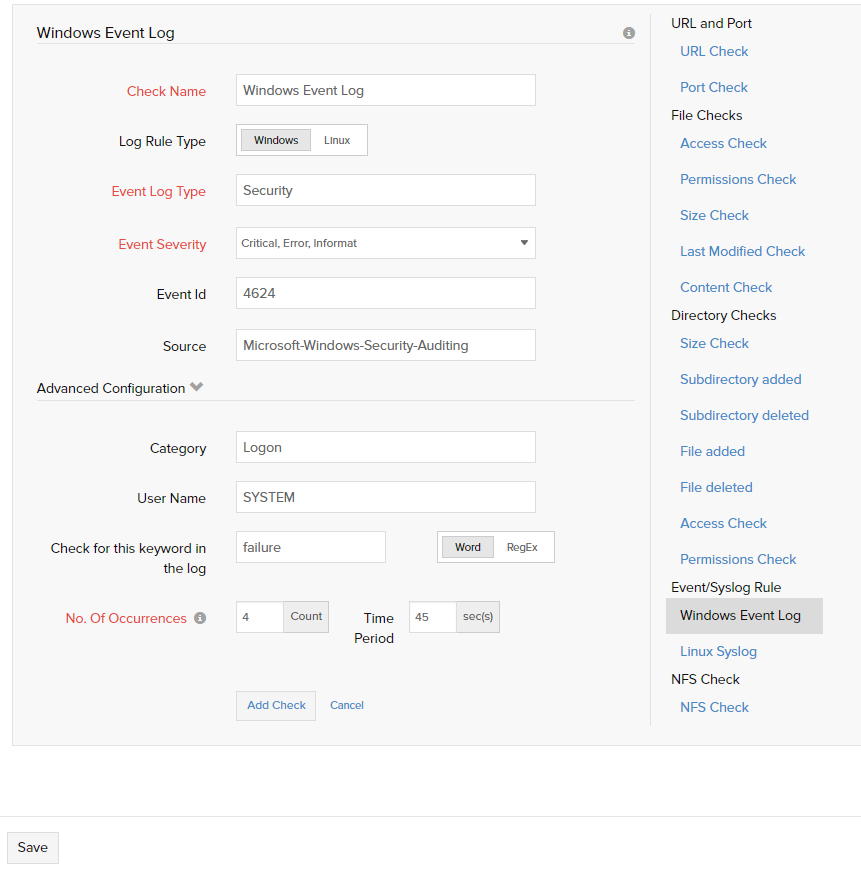
This rule can be added as another check to the resource check profile. This will filter the server's event log/syslog and search for a particular event. Alert is raised if the configured log rule event occurs and the monitor status is switched to trouble from up. If the monitor was already in trouble or down state, the status is unaffected but the event is logged in the log report.
For Windows servers, event log rule can be configured. An event log type should be selected from Windows standard types [Application, Setup, System, Security, Forwarded Events] or a custom (application specific) event log type. Event Severity level(s) must be selected and the check name must be specified. These are all the compulsory fields in the basic configuration. The optional fields are event id, and source. In addition to this advanced configuration may be setup for the log rule.
In advanced configuration, number of occurrences (maximum 45) is mandatory. This denotes the maximum number of configured event log entries that are allowed. For number of occurrences 'n' greater than 1, the timeout (maximum 45 seconds) must be mentioned. This denotes that the configured log type can occur for up to n times within the timeout and no alert will be triggered. Other advanced configuration options for the event filter are category, user name and a keyword to search for in the log.
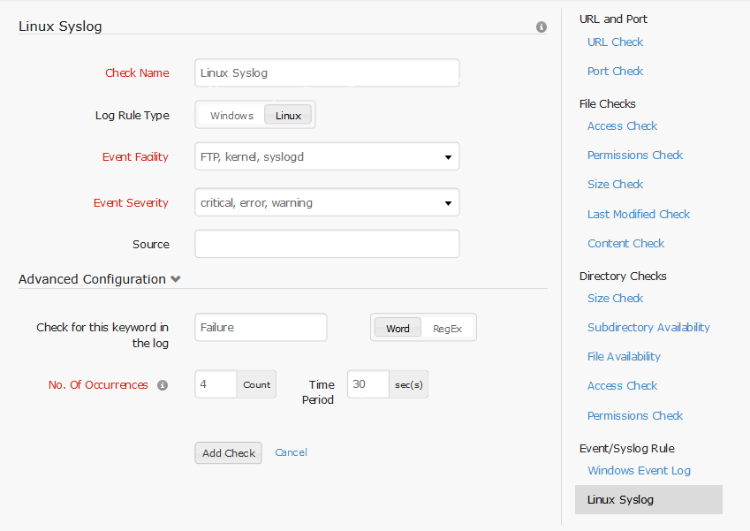
For Linux servers, syslog rule can be configured to filter certain rules. One or more event facility should be selected from Linux standard facilities [kernel, user-level, mail, system, authorization, syslogd, line printer, network news, UUCP, clock daemon, authpriv, FTP, NTP, log audit, log alert, cron, local0, local1, local2, local3, local4, local5, local6, local7]. The event severity level(s) must be selected and the check name must be specified. These are all the compulsory fields in the basic configuration. Optionally, the source can also be configured. In addition to this, some advanced configuration may be setup for the log rule.
In advanced configuration, number of occurrences (maximum 45) is mandatory. This denotes the maximum number of configured event log entries that are allowed. For number of occurrences 'n' greater than 1, the timeout (maximum 45 seconds) must be mentioned. This denotes that the configured log type can occur for up to n times within the timeout and no alert will be triggered. Optional advanced configuration option for the event filter is keyword to search for in the log.
In Syslog Alerting module, the agent will send alerts to the server instantaneously if all the check criteria's are matched. But if the alert happens frequently the agent will try to open a connection and send alert data to server repeatedly. For this we have put a restriction whereby the agent wont send the alert to server if it has been already sent in the past 1 minute.
A regular expression is a special string of text used to describing a search pattern. Any string of text is also a regular expression. In addition to plain text, regular expressions have a few special characters with special functions for matching string patterns (names). Regular expressions are an extension to wildcards. A popular wildcard is * used to denote any text. Using this wildcard the user can search for all txt format files by writing down *.txt. The regular expression equivalent for it would be .*\.txt. The first . is the symbol for any character, * represents that the preceding symbol or group can occur 0 or more times. The following \. denotes the character . and txt denotes the string txt.
Some common regular expression notations are
| ^ | Start of line |
| $ | End of line |
| . | Matches any character |
| \d | Matched digits 0-9 |
| \s | Matches whitespace |
| \S | Matches non whitespace |
| [A-Z] | Matches any capital alphabet. [] is used to represent a set. |
| [a-z] | Matches any small alphabet |
| * | Quantifier - Matches the preceeding group 0 to any number of times. |
| + | Quantifier - Matches the preceeding group 1 to any number of times. |
| (.*) | Capturing group that matches any character 0 to any number of times. |
| | | Or |
| ^([A-Z]*[a-z]*)$ | Capturing group to match a string with all capital letters or all small letters |
| ^(www\.site24x7\.com)$ | Matches www.site24x7.com. \ is an escape symbol. Anything following it is matched as is even if it is a special symbol. |
This is just a brief description of regular expression and its special symbols. This should be sufficient to form simple regular expressions. Although it is recommended to test the regular expression before using it to configure a resource check.
| Resource Check Category | Resource Check Name | Supported Packs | Edition | ||||
| Standard | Business | Advanced | Premier | Professional | Enterprise | ||
| Number of Allowed Checks count | 25 Checks | 25 Checks | 25 Checks | 25 Checks | 25 Checks | 25 Checks | |
| Number of Allowed Checks count | 25 Checks - Uniformly | ||||||
| URL | URL | √ | √ | √ | √ | √ | √ |
| PORT | Port | √ | √ | √ | √ | √ | √ |
| FILE MONITORING | Acess | √ | √ | √ | √ | √ | √ |
| Permission | √ | √ | √ | √ | √ | √ | |
| Size | √ | √ | √ | √ | √ | √ | |
| Last Modified | √ | √ | √ | √ | √ | √ | |
| Content | √ | √ | √ | √ | √ | √ | |
| DIRECTORY MONITORING | Size | √ | √ | √ | √ | √ | √ |
| Subdirectory Availability | √ | √ | √ | √ | √ | √ | |
| File Availability | √ | √ | √ | √ | √ | √ | |
| Access | √ | √ | √ | √ | √ | √ | |
| Permission | √ | √ | √ | √ | √ | √ | |
| EVENT/SYS LOG RULE | Windows Event log | Χ | Χ | √ | √ | Χ | √ |
| Linux Syslog | Χ | Χ | √ | √ | Χ | √ | |
Help Admin Adding a monitor Server Resource Check Profile
Site24x7 is a service by Corp.
